As we continue to fight against increasingly sophisticated cyberattacks, understanding the fundamental building blocks of these attacks is crucial. One of the most important concepts in cybersecurity is TTP – Tactics, Techniques, and Procedures. So, what is TTP in cybersecurity, and why should it matter to you?
In this blog, I’ll break down what TTPs are, how attackers use them, and most importantly, how you can leverage them to strengthen your organization’s security defenses. Whether you’re a seasoned security professional or just starting out, this guide will give you the knowledge you need to stay ahead of cyber threats.
What Are Tactics, Techniques, and Procedures (TTPs)?

Tactics in Cybersecurity
In cybersecurity, tactics refer to the overarching goals or objectives that attackers aim to achieve. For example, an attacker’s tactic might be to exfiltrate sensitive data or disrupt system operations. Understanding these tactics allows security professionals to identify the broad intent behind an attack.
Techniques in Cybersecurity
Techniques are the specific methods attackers use to achieve their tactics. For example, if an attacker’s goal is to exfiltrate data, they may use a technique like phishing or credential stuffing. Knowing the techniques attackers use allows defenders to set up measures that can block or mitigate these specific methods.
Procedures in Cybersecurity
Finally, procedures are the detailed, repeatable steps that attackers follow to execute a technique. This might include actions like using a specific phishing tool, modifying malware code, or exploiting a vulnerability in a particular software system. Procedures are the most granular aspect of TTPs, and they often vary depending on the attack.
How TTPs Are Used in Real-World Cyber Attacks

Now that we understand what TTPs are, let’s explore how they manifest in real-world cyberattacks. Attackers often rely on a combination of tactics, techniques, and procedures to execute successful breaches.
Real-Life Example: Ransomware Attacks
One of the most well-known tactics in cyberattacks is ransomware. The tactic here is clear: disrupt the victim’s operations and demand a ransom for restoration. To achieve this, attackers may use a variety of techniques such as phishing emails with malicious attachments or exploiting unpatched vulnerabilities.
A typical procedure might involve gaining access via a Remote Desktop Protocol (RDP) vulnerability, then deploying malware like Ryuk or Conti.
Once the ransomware is executed, the attacker demands payment and threatens to release sensitive data if the victim doesn’t comply.
By identifying the TTPs used in such attacks, organizations can better prepare and defend against these threats.
The MITRE ATT&CK Framework and TTPs
One of the best ways to understand TTPs and defend against them is by using the MITRE ATT&CK Framework.
This framework maps out the known TTPs of adversaries, providing a wealth of information that cybersecurity teams can use to detect, respond to, and mitigate attacks.
What is MITRE ATT&CK?
MITRE ATT&CK is a knowledge base of adversary tactics, techniques, and procedures based on real-world observations.
It categorizes TTPs into different matrices for Windows, Linux, Cloud, and other environments. The framework is invaluable for cybersecurity professionals because it allows them to:
- Identify the TTPs used in previous attacks
- Predict how attackers might attempt to breach their systems
- Deploy the right countermeasures to block attacks
By integrating the MITRE ATT&CK Framework into your threat detection and response strategy, you can better align your defenses with the tactics, techniques, and procedures most commonly used by cybercriminals.
How to Defend Against TTP-Based Attacks
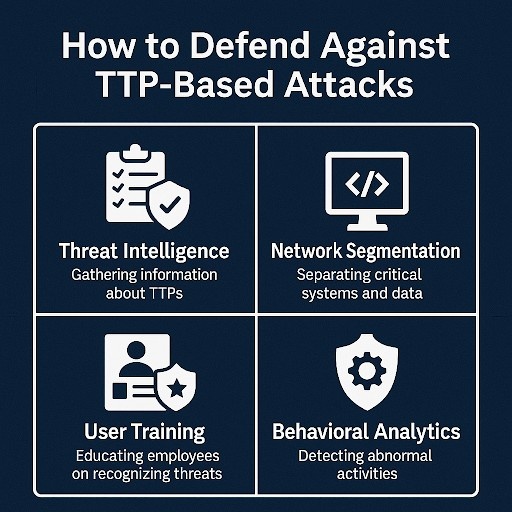
Now, let’s talk about defense. Knowing the TTPs attackers use isn’t just about identifying their moves—it’s about stopping them in their tracks.
1. Implement Multi-Layered Security
One of the best ways to defend against TTP-based attacks is to use a multi-layered defense strategy.
This includes combining tools like firewalls, intrusion detection systems (IDS), endpoint protection software, and threat intelligence feeds to create several barriers between attackers and your sensitive data.
2. Regularly Update and Patch Software
Many attackers exploit known vulnerabilities, so keeping your software up-to-date is critical. For example, attackers may use techniques like exploiting unpatched vulnerabilities in outdated software to gain access to your network. Regular patching ensures that these attack vectors are closed before adversaries can exploit them.
3. Employee Awareness and Training
Phishing, one of the most common techniques for initial access, can be mitigated through proper employee training. Teach your team to recognize suspicious emails, avoid clicking on unknown links, and report any strange activity.
4. Monitor and Analyze Network Traffic
Utilizing network traffic analysis can help you detect abnormal behavior that might indicate an attack is underway. Tools like SIEM (Security Information and Event Management) systems allow you to monitor network traffic and identify patterns that align with known TTPs.
5. Use Threat Intelligence Feeds
Leveraging threat intelligence can provide you with up-to-date information about emerging TTPs. By continuously feeding this data into your security systems, you can stay ahead of new techniques and procedures being used by cybercriminals.
TTPs in Incident Response and Threat Hunting
When an attack is imminent or in progress, cybersecurity teams must respond quickly. Incident response teams use TTPs to identify the attack’s origins and methods, while threat hunters actively search for signs of compromise within the organization’s network.
How TTPs Inform Incident Response
In incident response, identifying the specific TTPs an attacker is using can help teams to:
- Quickly assess the attack’s scope and mitigate the damage
- Isolate affected systems to prevent lateral movement
- Gather forensic data to analyze how the breach occurred and close future attack vectors
How TTPs Support Threat Hunting
Threat hunters use TTPs to proactively search for signs of a breach, focusing on the techniques and procedures attackers commonly use. By understanding the TTPs associated with various threats, they can hunt more effectively and spot potential issues before they turn into full-scale attacks.
FAQs
What does TTP stand for in technology?
TTP stands for Tactics, Techniques, and Procedures in technology and cybersecurity. It refers to the methods, tools, and strategies used by attackers to gain unauthorized access, disrupt operations, or steal data. Understanding TTPs helps cybersecurity professionals defend against threats by identifying common behaviors of cyber attackers.
What does TTPs mean in cybersecurity?
In cybersecurity, TTPs refer to Tactics, Techniques, and Procedures. These terms describe the specific actions taken by cybercriminals or threat actors to compromise systems.
Tactics are the broader goals, techniques are the methods used to achieve these goals, and procedures are the detailed steps followed to execute the techniques.
What is TPP in security?
In security, TPP can sometimes be confused with TTP, but it generally stands for Third-Party Provider or Third-Party Risk. It refers to the risks posed by external vendors or service providers that have access to an organization’s data or systems.
Managing TPP risk is crucial for maintaining cybersecurity, as third-party breaches can lead to vulnerabilities.
What does TTP stand for in SOC?
In a Security Operations Center (SOC), TTP stands for Tactics, Techniques, and Procedures, just like in cybersecurity. SOC teams use this framework to analyze and defend against attacks by recognizing patterns of behavior.
Understanding TTPs allows SOC analysts to detect threats, predict attack methods, and respond to security incidents efficiently.
Conclusion: The Power of Understanding TTPs in Cybersecurity
In conclusion, what is TTP in cybersecurity? It’s the knowledge of the tactics, techniques, and procedures that attackers use to compromise systems, exfiltrate data, or disrupt operations. Understanding these TTPs not only helps you defend against known attacks but also allows you to predict and prevent future ones.
By utilizing frameworks like MITRE ATT&CK, keeping your systems up to date, training your team, and leveraging the right tools, you can significantly enhance your cybersecurity posture. Remember, in today’s world, staying ahead of attackers means understanding their methods and being proactive. Stay safe out there, and always be prepared to adapt to new TTPs as they emerge!












